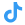Key Takeaways
- Open-source security demands a multi-layered approach — the same transparency that enables collaboration can also introduces security risks.
- Major risks include unpatched vulnerabilities, supply chain attacks, and abandoned or poorly maintained projects.
- Effective mitigation starts with continuous patching, strong access controls, and system hardening.
Open-source software has revolutionized the technology landscape, powering everything from personal computers to complex enterprise systems. Its collaborative nature, transparency, and cost-effectiveness have made it a cornerstone of modern computing.
However, this also presents unique security challenges. Since the source code is publicly accessible, the potential for security vulnerabilities and exploits is significantly amplified.
In this article, we explore best practices for strengthening open-source security — covering everything from supply chain risks to licensing compliance — with particular attention to securing Linux systems, which form the backbone of many open-source deployments.
What Is Open-Source Security?
Open-source security is the practice of protecting open-source software and its dependencies from vulnerabilities, misconfigurations, and supply chain threats. This is a critical concern due to the inherent nature of open-source platforms. While the transparency of open-source code accelerates vulnerability discovery and patching compared to closed-source models, it also means that attackers can study the codebase to find weaknesses.
Despite these challenges, the open-source community has fostered a strong culture of security awareness. Many projects benefit from a large number of eyes reviewing the code, which can help identify and address vulnerabilities early on.
Open-Source Security Risks

Open-source platforms, including Linux, offer significant advantages in terms of cost, customization, and community-driven development. However, their open nature also exposes them to unique security challenges.
Here are some of the primary risks associated with open-source software:
Known Vulnerabilities
With code accessible to everyone, the potential for vulnerabilities and exploits is significantly amplified. This means that vulnerabilities can be identified and exploited more quickly by malicious actors.
Code Quality and Security Practices
Inconsistent coding standards and security practices across open-source projects can lead to vulnerabilities. Some contributors may lack the expertise or focus on security, increasing the risk of flawed code. Additionally, the rapid development cycle — driven by new features and bug fixes — can outpace thorough security testing, allowing flaws to persist unnoticed.
Dependency Chain Vulnerabilities
Many open-source projects rely on third-party libraries, which can introduce vulnerabilities that propagate through the entire software ecosystem. A flaw in one dependency can affect multiple projects, increasing the risk.
Supply Chain Attacks
Attackers may target the software supply chain by inserting compromised components into open-source projects. This can lead to widespread distribution of malicious code within otherwise trusted software.
Unverified Contributors
The open-source model often includes contributions from a wide and diverse group of developers. Ensuring the trustworthiness of every contributor is challenging, increasing the risk of malicious code being introduced.
Abandoned Projects
Some open-source projects may be abandoned by their original developers, leaving known vulnerabilities unaddressed. Users of these projects are at risk if they continue to rely on unmaintained software.
Reverse Engineering
The availability of open-source code allows attackers to analyze it for vulnerabilities, potentially developing exploits that can be used against systems relying on that code.
Social Engineering Attacks
Open-source communities can be targets for social engineering, where attackers manipulate individuals to gain access to sensitive information or alter project code with malicious intent.
License Compliance
Misunderstanding or failing to comply with open-source licenses can result in legal challenges and financial penalties. It’s essential to ensure that all licenses are properly followed when using open-source components. This risks also extends to reusing code from open-source projects without proper attribution or understanding the associated license terms.
Why You Shouldn’t Ignore Open-Source Security
Given the pervasive risks outlined, ignoring open-source software security isn’t optional — it’s mission-critical. One vulnerable package can expose your entire infrastructure, trigger compliance violations, and damage your organization’s reputation. The Log4Shell incident proved how deeply embedded — and dangerous — open-source dependencies can be.
Since most modern systems rely on open-source at every layer, securing it must be a top priority. Start by auditing your OSS usage, prioritizing continuous patching, and using tools like TuxCare’s KernelCare Enterprise to automate Linux security and reduce risk.
Open Source Security: 8 Must-Follow Best Practices
To mitigate risk and build secure open-source systems, organizations must adopt proven security practices. Integrating these into the development and operations lifecycle strengthens your overall security posture and lessens exposure to vulnerabilities.
1. Adopt Secure Coding Practices
The Heartbleed bug, a critical security flaw in OpenSSL, highlighted the importance of secure coding practices. To protect applications from vulnerabilities, it’s essential to employ secure coding techniques into the entire development lifecycle.
Key practices include:
- Secure by Design: Incorporate security considerations into the early stages of software development.
- Threat Modeling: Identify potential vulnerabilities and risks through threat modeling.
- Coding Standards: Adhere to established secure coding standards and guidelines.
- Error Handling: Implement robust error handling to prevent information leakage and denial-of-service attacks.
- Code Reviews and Testing: Conduct thorough code reviews and security testing to identify and address vulnerabilities.
- Dependency Management: Carefully select and manage third-party libraries to minimize risks.
2. Regularly Update and Patch Software
Open-source platforms frequently release patches and updates that address vulnerabilities. Failure to apply these updates promptly can leave systems exposed to exploitation, leading to data breaches, system downtime, and financial loss.
- Prioritize Security Updates: Focus on critical patches that address high-severity vulnerabilities first.
- Automate Updates: Use tools like Ansible, Chef, or Puppet to automate the update process across multiple systems. For Linux systems, you can leverage KernelCare Enterprise to automate the kernel patching process without having to reboot them.
- Test Before Deploying: Always test updates in a staging environment before deploying them to ensure they do not introduce new issues.
- Stay informed: Subscribe to security mailing lists and advisories to stay informed about new vulnerabilities and patches.
3. Strong Access Control Mechanisms
Controlling who has access to your systems and what they can do is a critical component of security. Open-source platforms often provide granular access control features that, when configured correctly, can significantly reduce the risk of unauthorized access and data breaches.
- Least Privilege Principle: Grant users only the minimum permissions necessary to perform their job functions. This significantly limits the potential damage caused by compromised accounts.
- Role-Based Access Control (RBAC): Manage user permissions based on roles, simplifying administration and improving security.
- Multi-Factor Authentication (MFA): Enable MFA to add an additional layer of security, making it difficult for attackers to gain access using stolen credentials.
4. Harden the Operating System
A hardened operating system acts as a robust foundation for your IT infrastructure. By reducing the attack surface and implementing defensive measures, you make it more difficult for attackers to compromise your systems.
- Apply security updates promptly: Keep your operating system and installed software up to date with the latest patches to address vulnerabilities.
- Disable unnecessary services: To reduce potential attack vectors, turn off services and daemons that are not required.
- Configure firewalls: Implement strict firewall rules to control inbound and outbound traffic, allowing only essential services.
- Enforce strong user access management: Create strong password policies, manage user accounts effectively, and prevent privilege escalation.
5. Audit and Monitor System Activity
Continuous monitoring and auditing are essential for detecting and responding to security incidents in real time. By gaining visibility into system activity, organizations can identify anomalies, prevent data breaches, and comply with security regulations.
- Implement centralized logging: Collect logs from various system components into a centralized repository for efficient analysis.
- Deploy intrusion detection systems (IDS): Use IDS tools like Snort or OSSEC to identify suspicious activity and potential intrusions.
- Regular Audits: Perform regular security audits to review user activity, system configurations, and access logs. Tools like Lynis can automate much of this process for Linux systems.
6. Maintain a Complete OSS Inventory
You can’t secure or patch what you don’t know you’re using. Many breaches occur because organizations lose track of outdated or vulnerable open-source components embedded deep within their infrastructure.
Build a Real-Time Inventory: Use Software Composition Analysis (SCA) tools like Syft, Grype, or Anchore to automatically detect and catalog every OSS component in use, including nested dependencies.
Classify by Criticality: Tag components based on system importance and risk level to help prioritize patching and updates.
Schedule Regular Audits: Treat OSS inventories as living documents. Perform monthly or quarterly reviews to identify unmaintained or end-of-life packages.
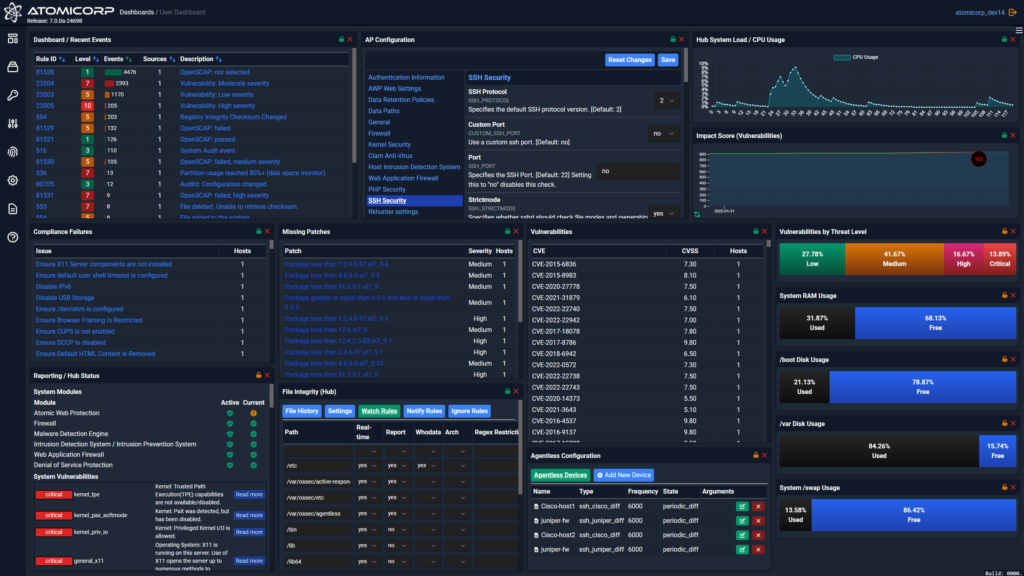
Plan for Unsupported Components: If you rely on older software that has lost official support, use services like TuxCare’s Endless Lifecycle Support (ELS) to continue receiving security patches and stay compliant. ELS is available for end-of-life Linux distributions, programming languages like Python and PHP, and frameworks such as .NET, Spring, and AngularJS.
7. Enforce License Compliance
Open-source doesn’t mean “free for all.” Each component comes with its own legal requirements, and non-compliance can lead to severe consequences — ranging from public takedowns to lawsuits.
Automate License Detection: Use tools like FOSSA, ClearlyDefined, or OpenChain to scan and identify license types (GPL, Apache, MIT, BSD, etc.) within your codebase.
Map Dependencies to Business Risk: Determine if any license introduces obligations such as disclosure or redistribution, which may conflict with your company’s IP or distribution model.
Document Usage Rules: Maintain clear internal documentation that outlines how each OSS license type may be used, redistributed, or modified within your organization.
Review Before Deployment: Make license checks part of your CI/CD pipeline to prevent license violations from reaching production.
8. Use Trusted and Actively Maintained Components
Not all open-source software is equal. Some projects are backed by large communities and regular updates — others may be abandoned, poorly documented, or ripe for exploitation.
Prioritize Active Projects: Select packages that show consistent release activity, bug fixes, and community engagement on platforms like GitHub or GitLab.
Assess Maintainer Reputation: Review the project’s history, number of contributors, and how quickly it addresses issues or pull requests.
Avoid Single-Maintainer Projects for Core Functions: These can quickly become risks if the maintainer steps away or becomes compromised — the XZ Utils backdoor is a recent reminder of this danger.
What Makes Linux Security Unique in Open Source?
Linux is the backbone of the open-source ecosystem, powering everything from servers and containers to cloud infrastructure. But its widespread use also makes it a prime target for attackers. The Linux attack surface is vast and modular — extending from user-space applications down to the very core: the kernel.
This deep integration makes kernel vulnerabilities especially critical. A single flaw can compromise the entire system and requires immediate, targeted action. That’s why truly proactive, kernel-level patching is essential.
Traditional patching often leads to downtime — a cost modern enterprises can’t afford. TuxCare’s KernelCare Enterprise solves this problem with rebootless patching that keeps your Linux systems continuously secure and disruption-free.
Secure Linux Systems with TuxCare
Open-source software delivers unparalleled flexibility and innovation, but it also brings security risks that require a proactive, multi-layered defense. By adopting best practices and staying vigilant, organizations can minimize their attack surface and better protect their infrastructure.
TuxCare’s KernelCare Enterprise provides automated, rebootless patching for all major enterprise Linux distributions including CentOS, RHEL, AlmaLinux, Rocky Linux, Ubuntu, Amazon Linux, CloudLinux, and more.
Protect your Linux systems, eliminate downtime, and simplify patch management — all with one powerful solution.



 Documentation
Documentation Login
Login